Aws Cloudformation Template Validator

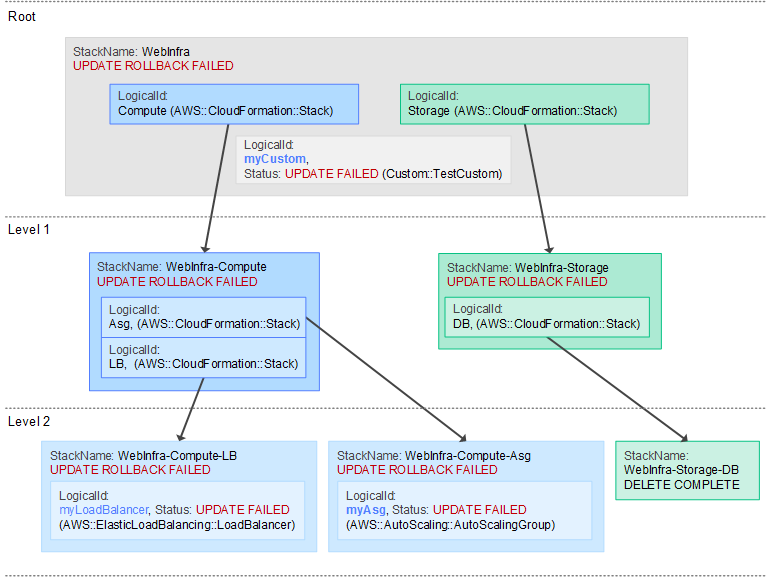
Certificate validator is an aws cloudformation custom resource which facilitates acm certificate validation via dns.
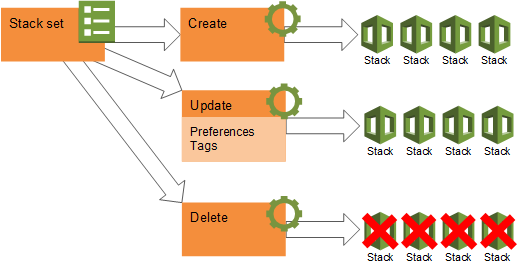
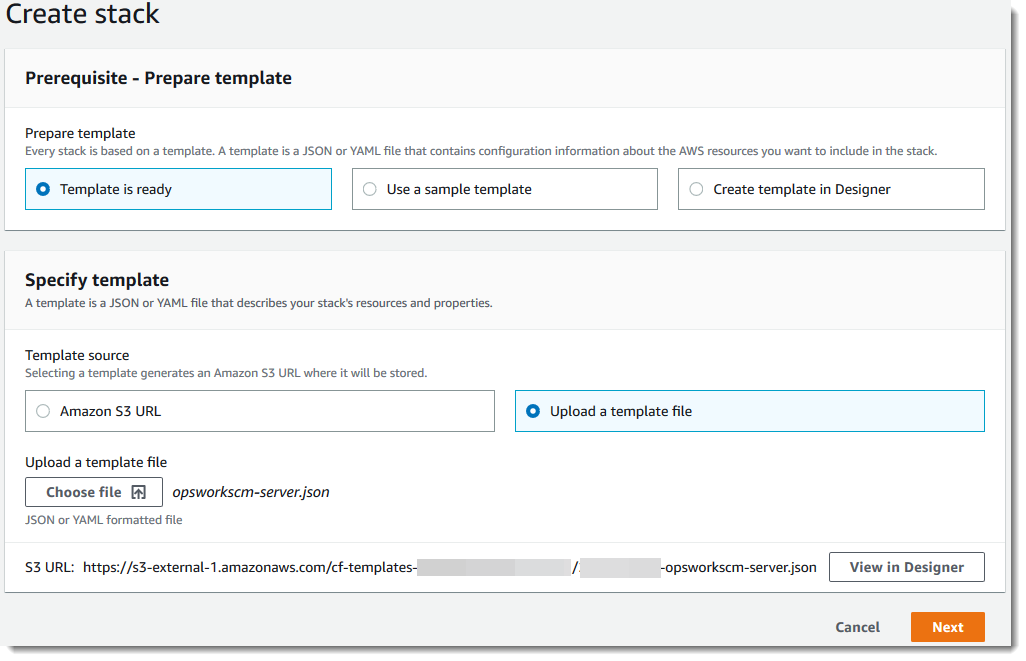
Aws cloudformation template validator. Nor does it determine the number of resources that will exist when the stack is created. Create your stack with aws cloudformation designer. Validate your json syntax with a browser based tool text editor or a command line tool such as the aws command line interface aws cli template validator. It has no dependencies and is thoroughly tested under python 2 7 python 3 3 python 3 4 python 3 5 python 3 6.
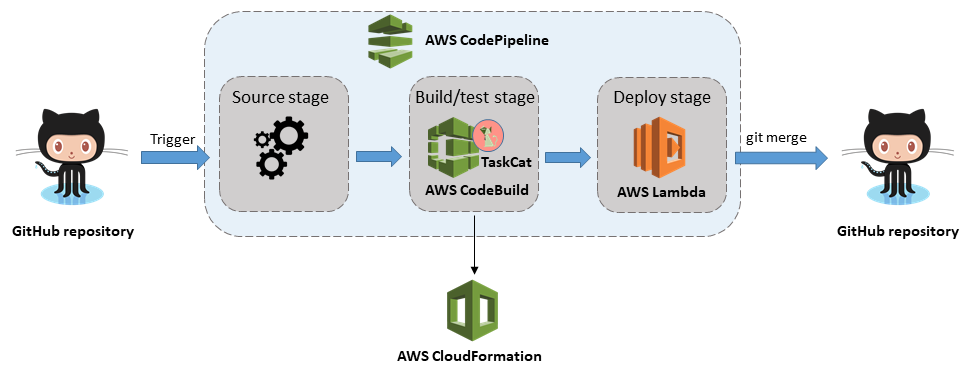
Cfn nag scan input path cfn volume encrypted yml now that you have run failure and success scenarios against cloudformation templates using cfn nag you will provision a full aws infrastructure solution using mu and then integrate cfn nag into the deployment. A custom resource allows you to write custom provisioning logic in templates that aws cloudformation runs anytime you create update or delete stacks. If you ve used this command before you might also know that this validator only checks the syntax of your template. Cloudformation validator provides type checking and other base functionality out of the box and is designed to be non blocking and easily extensible allowing for custom validation.
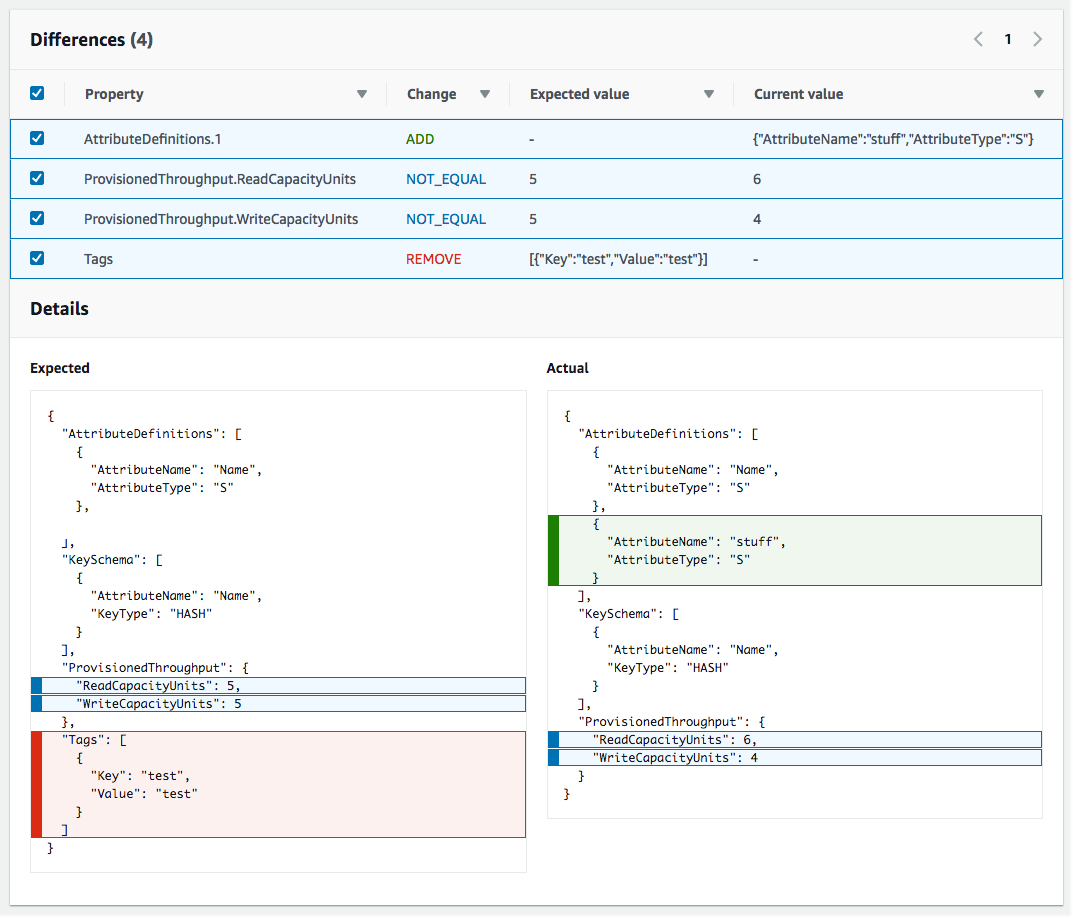
If both these checks fail aws cloudformation returns a template validation error. Aws cloudformation first checks if the template is valid json. It does not ensure that the property values that you have specified for a resource are valid for that resource. Using cfn lint to validate your cloudformation template if you ve used cloudformation before you ll already know about the validate template command on aws cli.
For cloudformation syntax validation one option is to use the aws cli to call the validate template command. To follow proper json or yaml syntax in your aws cloudformation template consider the following. The aws cloudformation validate template command is designed to check only the syntax of your template. Usage python cf validator py cf path cf template file cf rules rules file cf res resource file allow cap no region us east 1.
For security and resource management another approach is to run a jenkins pipeline from an amazon ec2 instance under an ec2 role that has been granted only the necessary permissions.